Connecting your computers to WireGuard VPN hosted in MikroTik
In our previous tutorial we showed how to set up a WireGuard server in our MikroTik CHR.
If you still did not set up a WireGuard server on your CHR, you can set up one in just a couple of minutes.
In this tutorial we will show you three ways on how to connect your computer to your newly created WireGuard VPN server.
For this tutorial we reccommend using the latest version of WinBox, which can be downloaded here, or WebFig, which can be accessed via a web browser. This way we can easily use the configuraion generated by RouterOS.
Downloading the WireGuard client
We will start by installing the WireGuard app. If you use Windows or MacOS, go to https://www.wireguard.com/install/ and download the appropriate installer.
If you use Linux, you need to install wireguard through the terminal first.
$ sudo apt install wireguardThen you can download and install WireGUIrd to manage the connections more easily through a GUI, like in Windows and macOS
After you finish with the installation, you can choose one of the following methods to add and connect your device to your Wireguard VPN.
Method 1: Using RouterOS to generate the configuration.
This method is easier if you want to send the configuration to anyone you want. Your MikroTik device stores all the keys and configurations for all your peers.
We will start by going to Wireguard>Peers on our CHR. From there click on “+” and enter the following settings:
Interface: The Wireguard interface you will connect to(if you have more than one Wireguard interface)
Private Key: auto – this will let RouterOS to generate the key pair for you
Endpoint port: the Listening port of your Wireguard interface, configured in the previous tutorial, default 13231
Allowed Address and Client Address: An address that will be assigned to your device, it must be from the same network as the Wireguard interface.
Client DNS: The DNS server that the client will use, You can also set the address of a local DNS that you run locally in the MikroTik as container.
Client Endpoint: The IP address/domain of your CHR
Then click on OK to save the peer.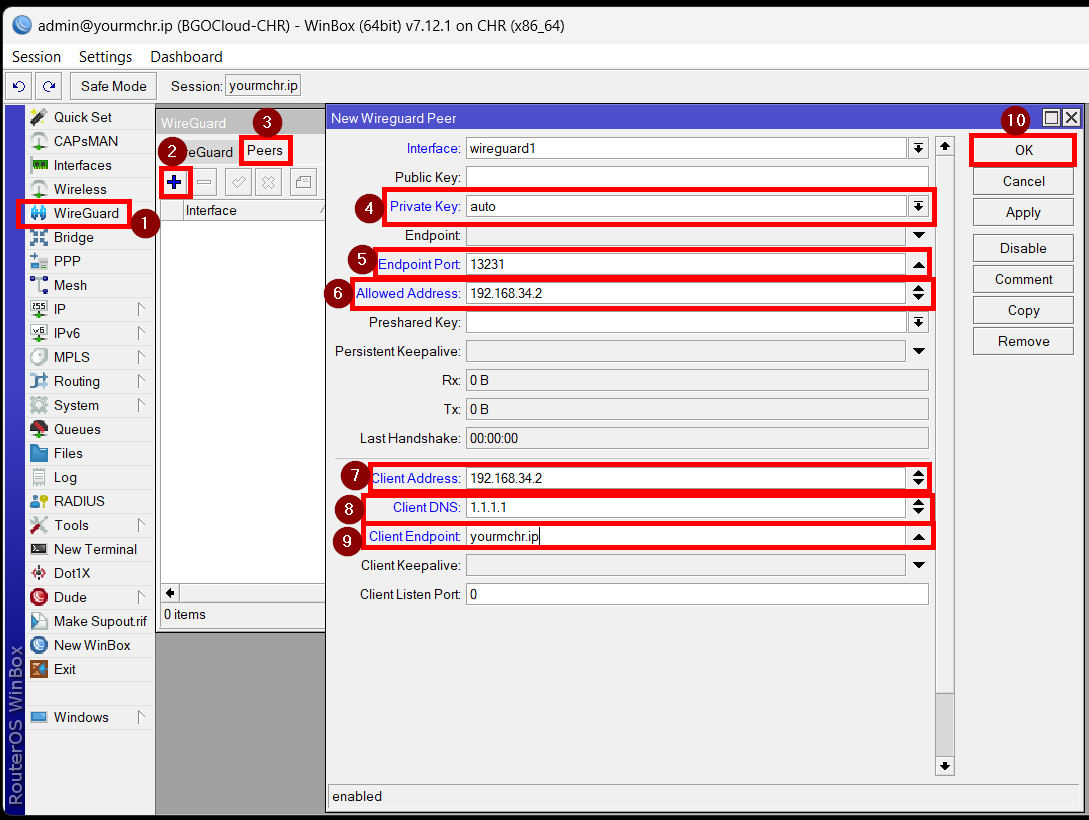
You can also add a comment to the peer to distinguish it more easily from the other ones. Click on Comment and enter the comment, click on “OK” to save it.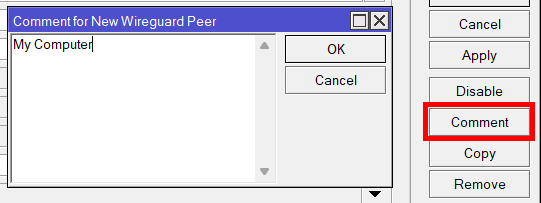
After everything is entered and saved, the configuration should be generated from your CHR. To find it scroll a little bit down on the peer window.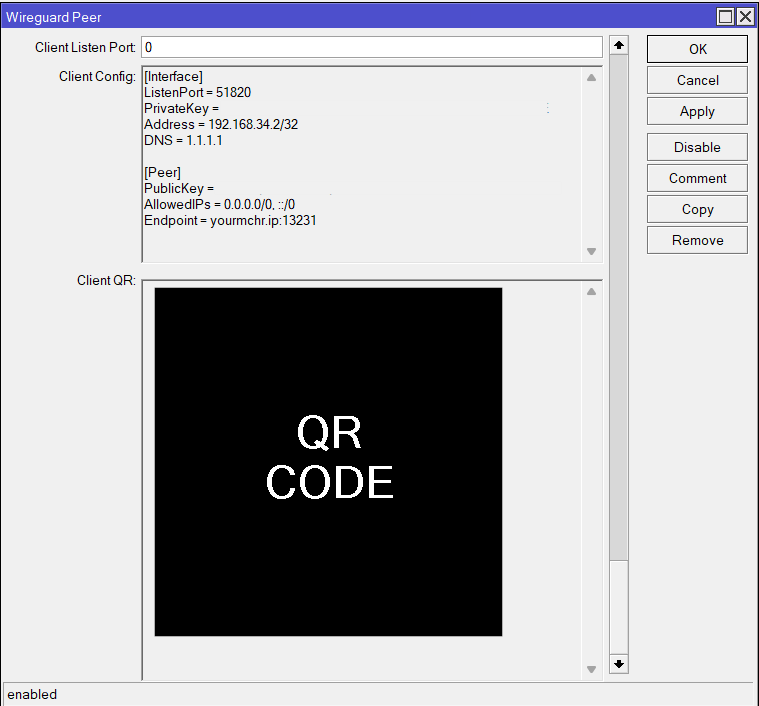
Open the WireGuard app and add an empty tunnel:
Then copy the whole configuration from the CHR to the app. Remove the Listen port to randomize the port every time you connect. Name it as you like and save it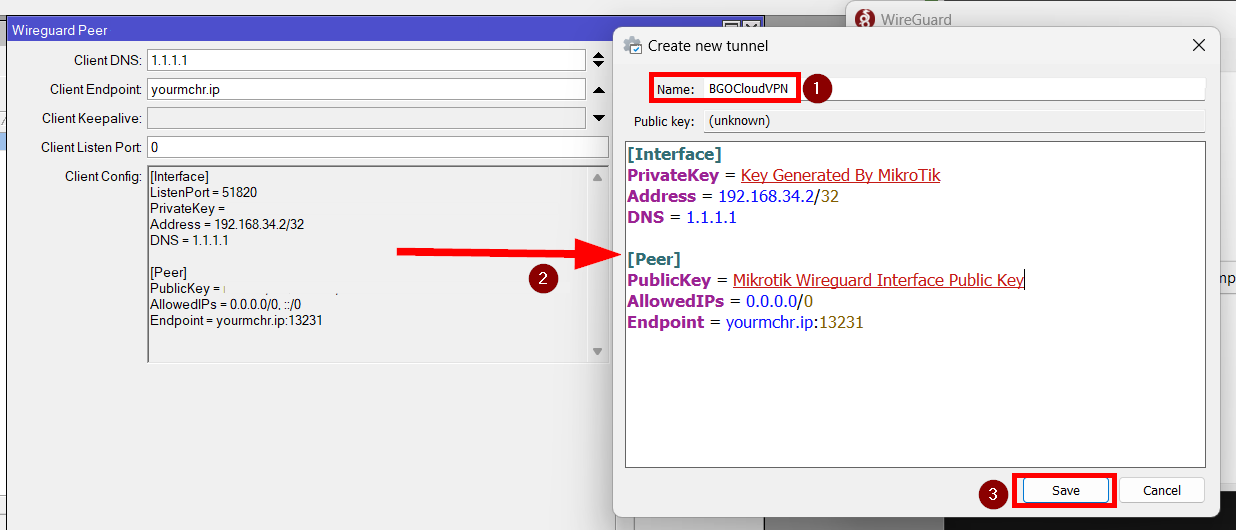
Now click on “Activate”. The app will establish a connection with the WireGuard server.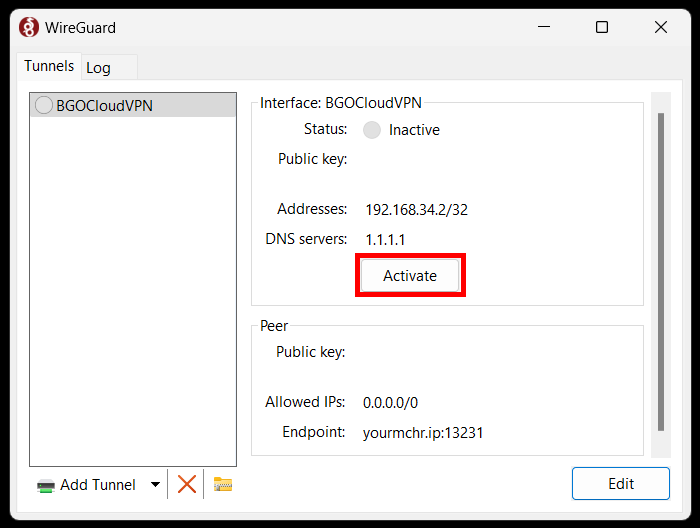
If the connection is successful, you should have internet access and a full traffic redirection to your VPN server. If you do not have internet access, you have to recheck your settings and try again.
Method 2: Importing a tunnel from a tunnel file
With this method you can make tunnel files and send them to your VPN users easily and quickly, or just have a backup.
In this method, you will need to know your WireGuard interface's public key, you can either use keys generated from the wireguard app or RouterOS. In this example we will use a peer generated from RouterOS.
After the peer is created in RouterOS, or you have keypair generated. Copy this example configuration into a .conf file, using your favourite text editor, and change it with your data:
[Interface]
PrivateKey= #<Key generated from the WireGuard App>
Address = #The Allowed address that you configured in your CHR, E.g.192.168.34.2/32
DNS = #The DNS that the peer will use, E.g. 1.1.1.1
[Peer]
Public Key = #<The Public key, copied from the MikroTik WireGuard Interface>
AllowedIPs = 0.0.0.0/0, ::/0 #This allows full traffic redirect, if you want redirect for specific addresses only, change this.
Endpoint = yourmchr.ip:13231 #Your CHR’s public IP address with WireGuard Listening port
After you've saved the tunnel configuration, open the app, click on "Add Tunnel" and locate the configuration file.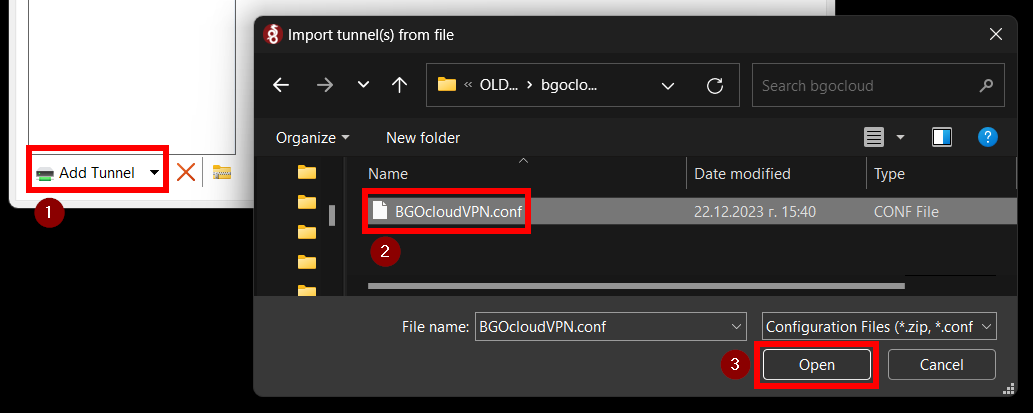
After that the tunnel will appear in the list with the file name. Click on "Activate" to check the connection.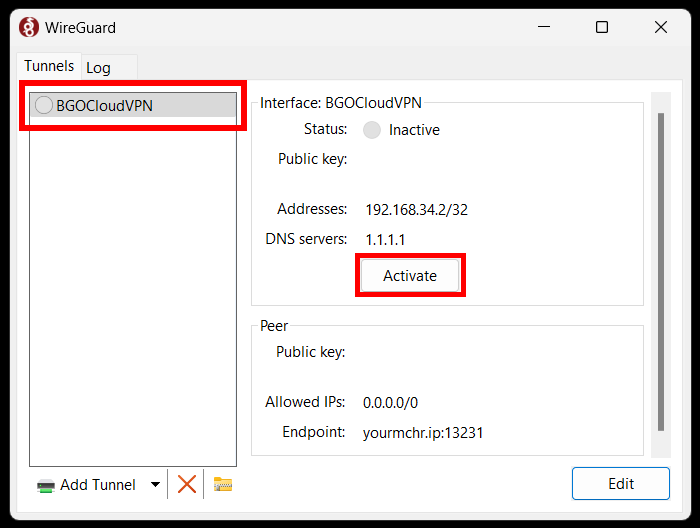
You can now connect to your new Wireguard server. You can check these articles to see how to connect other devices or how to create your Wireguard server hosted in your CHR.
Setting up WireGuard VPN in MikroTik CHR
Connecting Android and IOS devices to your WireGuard servers
You can also check our powerful MikroTik CHR plans and choose a suitable plan to get started.

