MikroTik CHR: Basic system protection (+ video)
Guide for essential system protection.
First to consider! If You leave service ports standard and don’t change the username and password as soon as possible, the chance to be compromised is enormous.
Here You will find the essential steps to protect your MikroTik CHR from intrusion.
Here's a small video explaining the process:
Be careful while placing restrictive (drop) rules, it is possible to limit your own access to the router.
Use "Safe Mode" button while you are not sure what the changes may cause.
In CLI "Safe Mode" is enabled/disabled with [Ctrl]+[X] combination.
Remember to release "Safe mode" after all changes are confirmed as working properly, otherwise they will be reverted once You log-out.
1. First and most important:
Create new username and password with Full privileges
[admin@mikrotik] > user add group=full name=newadmini password=H@rDt0Gu3SsP@sSw0Rd
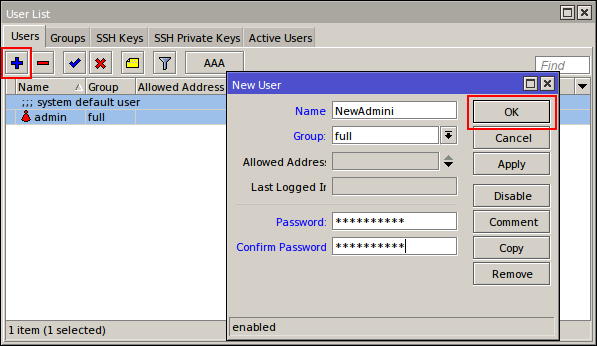
Delete the default one
2. Modify service ports so that unused services are disabled, and those who will be used is not on it’s default ports. It is very useful against bots. Use ports of your choice, but not overlapping reserved system ports.
https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers#Well-known_ports
For example:
Disable API, API-SSL, Telnet, FTP, WWW and WWW-SSL.
[newadmini@mikrotik] > ip service disable api,api-ssl,ftp,telnet,www,www-ssl
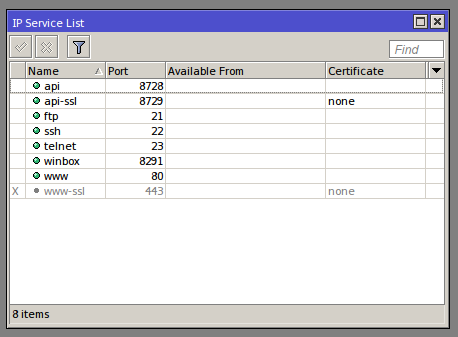
Change port for SSH from 22 to 22221
[newadmini@mikrotik] > ip service set ssh port=22221
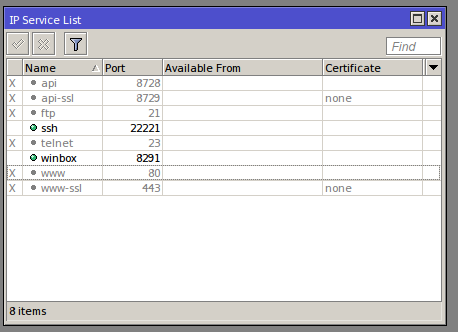
WinBox port should NOT be changed because the Windows App doesn’t support specifying destination port.
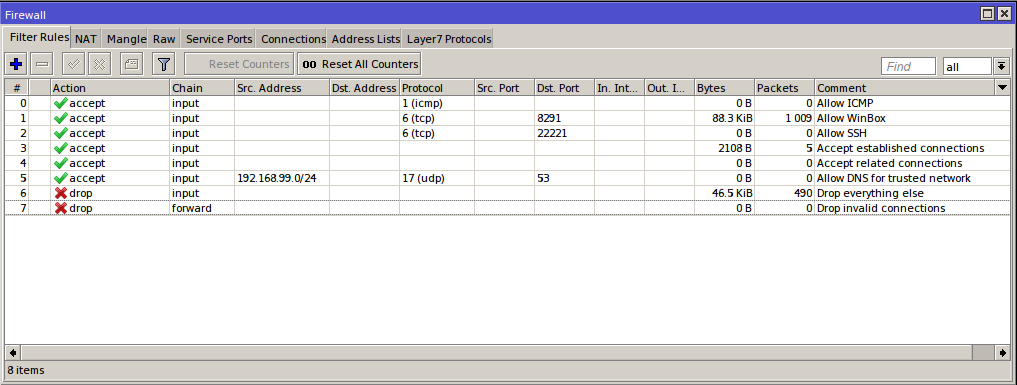
3. Add firewall/filter rules:
Chain INPUT:
[newadmini@mikrotik] > ip firewall filter add action=accept chain=input comment="Allow ICMP ping" protocol=icmp
[newadmini@mikrotik] > ip firewall filter add action=accept chain=input comment="Allow WinBox" dst-port=8291 protocol=tcp
[newadmini@mikrotik] > ip firewall filter add action=accept chain=input comment="Allow SSH" dst-port=22221 protocol=tcp
[newadmini@mikrotik] > ip firewall filter add action=accept chain=input comment="Accept established connections" connection-state=established
[newadmini@mikrotik] > ip firewall filter add action=accept chain=input comment="Accept related connections" connection-state=related
[newadmini@mikrotik] > ip firewall filter add action=accept chain=input comment="Allow DNS for trusted network" dst-port=53 protocol=udp src-address=192.168.99.0/24
[newadmini@mikrotik] > ip firewall filter add action=drop chain=input comment="Drop everything else"
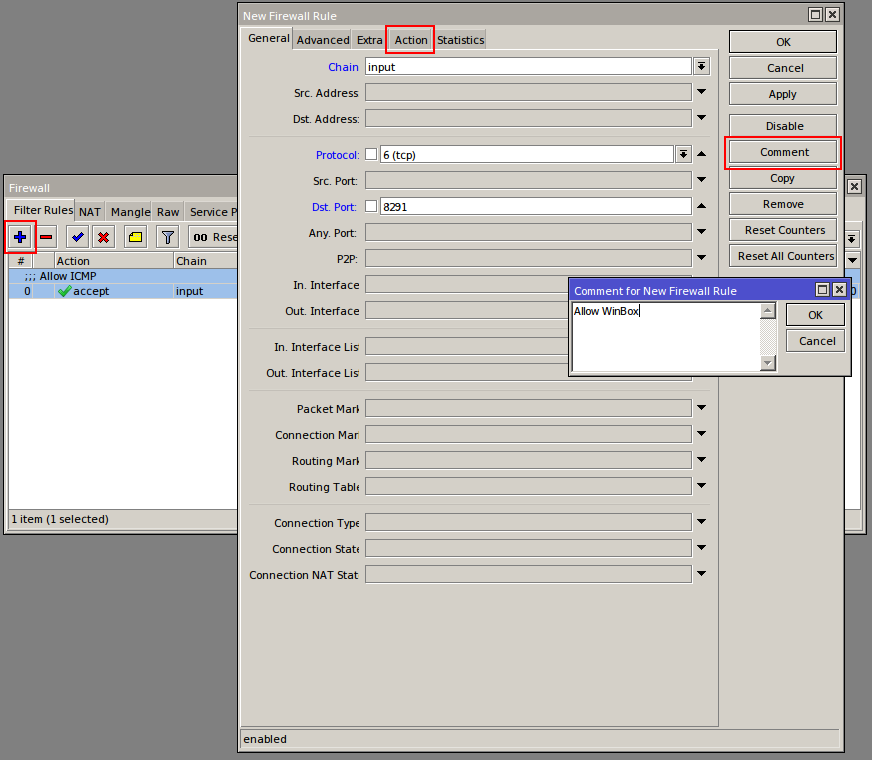
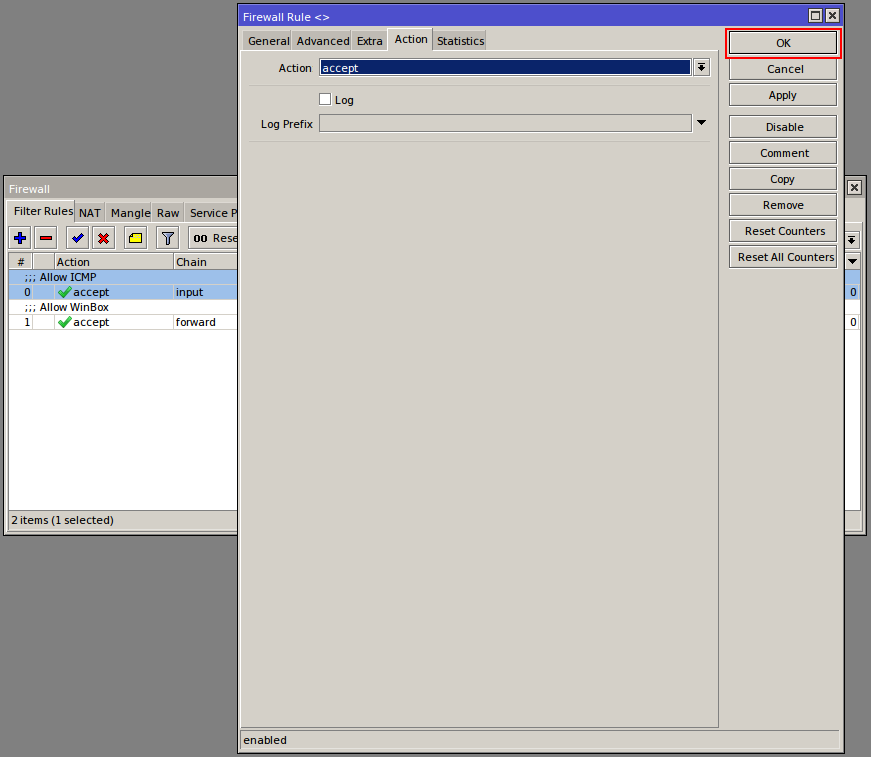
Chain FORWARD:
In Cloud Hosted Router, forwarding table might be very different depending on the particular use scenario.
[newadmini@mikrotik] > ip firewall filter add action=drop chain=forward comment="Drop invalid connections" connection-state=invalid
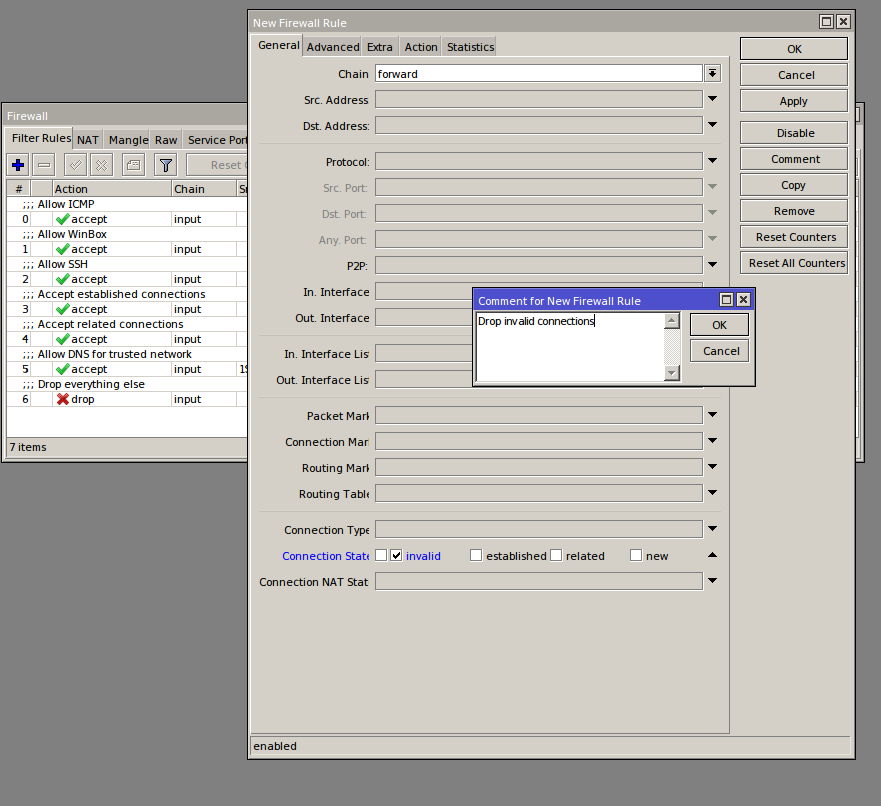
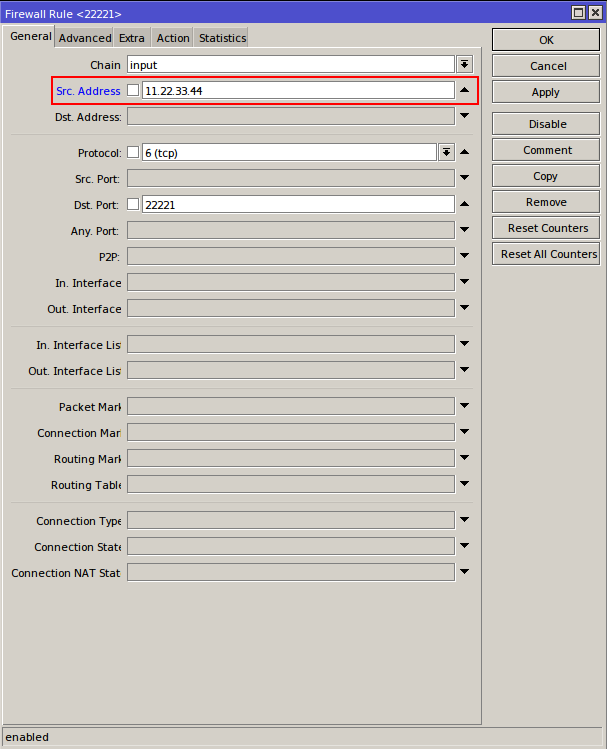
4. Optional: For better security, You can easily restrict the access to the router, by accepting only your home or office IP address from which you will modify router’s configuration:
This should be done for all rules that accepts connection on service ports (SSH and WinBox).
Please, be noted that the above firewall rules are NOT complete protection! It is only the very basic rules, and they should be appended or modified according to the real set-up!

