MikroTik CHR How to set-up L2TP VPN Server. VPN server for Apple devices - Iphone, MacBook. (+ video)
As we know, Apple does not support PPTP VPN protocol on its own devices.
One of the protocols supported by Apple devices is L2TP/IPsec.
In this Knowledgebase article, we will show you how to configure a MikroTik VPN server with L2TP with IPSec.
Here's a small video explaining the process:
First of all, You have to choose one of our MikroTik CHR VPS packets.
When you already have your own MikroTik CHR, you have to access the router and set a password to the admin account and made some security updates.
Please follow this article (MikroTik CHR: Basic system protection) for necessary system protection for your MikroTik Router.
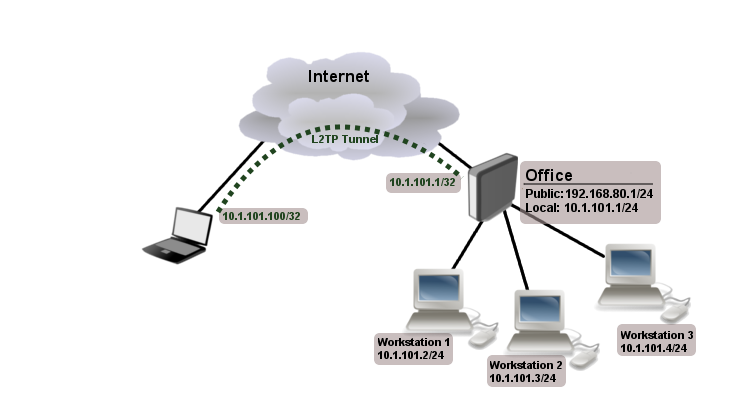
An example diagram gives an idea of what needs to be done
We will try to follow this diagram. Unfortunately, the Public IP address of our router will be different. In our scenario, it is 78.142.25.35
Open your browser and access MikroTik CHR and login with your admin account and your password.
If you access the router through a web browser you will see this:
Press only the WebFig button:
It is essential to make sure that our router is up to date.
Please, follow these steps and make the update of your router: (If your router is already up to date you can skip this step)
From left-side menu we choose: System --> Packages --> Press Check for Update
When you click Check for Update, if your router OS is not latest version, you can choose Download and Install option.
This option will download the latest version of Router OS and install it. The router will be restarted automatically.
After the restart, you have to login again and press the WebFig button.
In our case, I will add a bridge interface to our router and name it "local."
Maybe you already have some bridge and local IP address. You can use it. It is not mandatory to do this if you already have configured network topologies.
You can add fast and easy the new bridge with this command in Router OS terminal:
[admin@MikroTik] > interface bridge add name=local
Or you can make it from Web interface or Winbox:
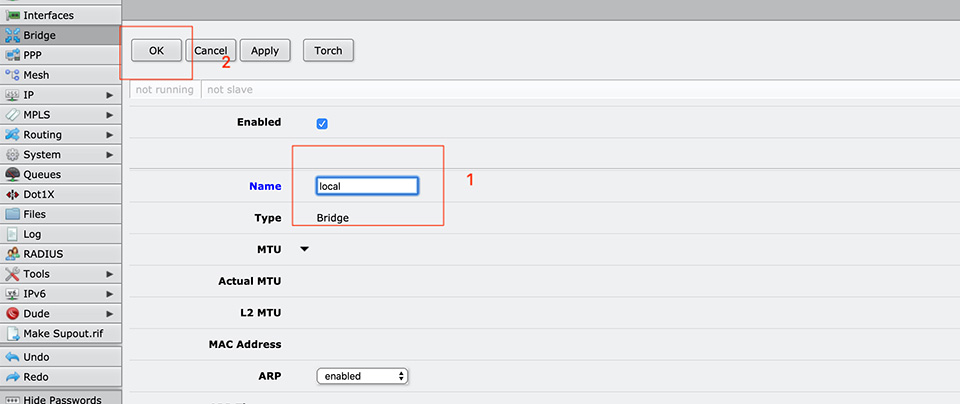
We can see the result in the Interfaces tab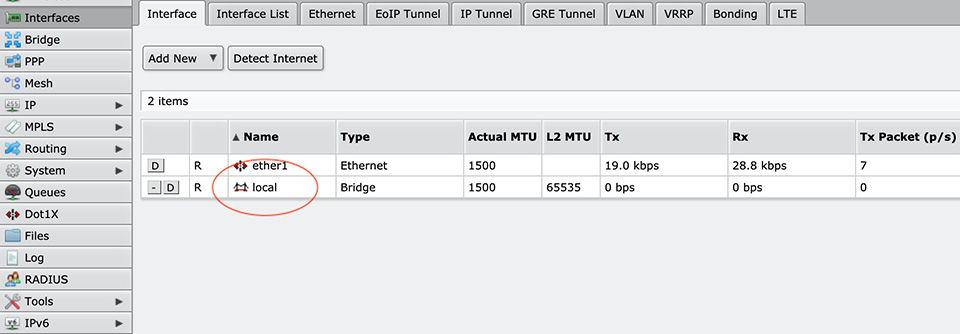
Now it is time to set an IP address for our Local network.
We are looking from the first pictures, and the IP address will be: 10.1.101.1 with netmask 255.255.255.0 (10.1.101.1/24) and place it on the "local" interface.
If you have your IP address configured, you can skip these steps. You can use the IP address from your network topology.
It can be done easily with this command in MikroTik OS terminal:
[admin@MikroTik] > ip address add address=10.1.101.1/24 interface=local
You can add it thought WEB or Winbox.
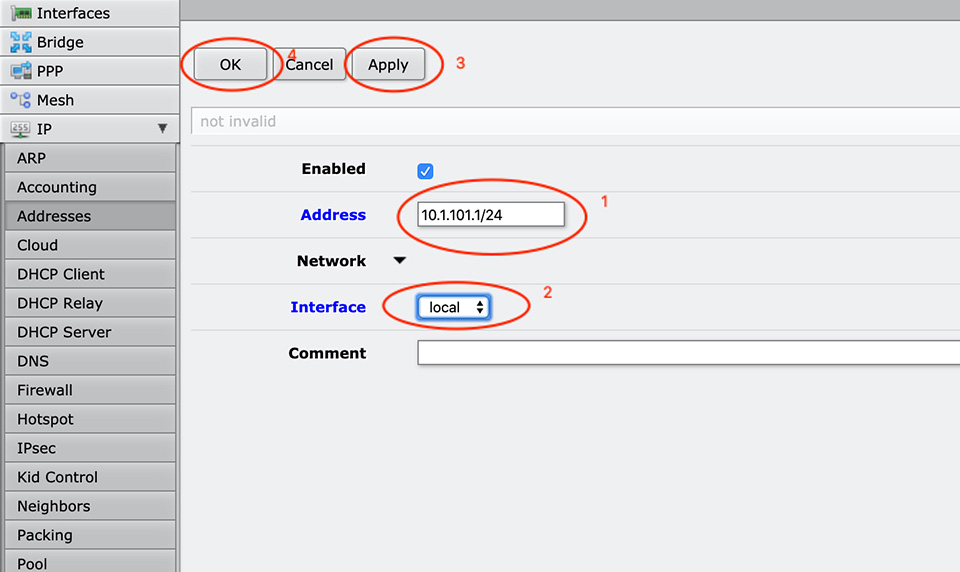
Now we have our Mikrotik Router with Public IP address and Private One.
It is a good idea to add IP Pool from where our L2TP customers will receive their IP addresses.
The easiest way to do this is with this command in MikroTik Router Os Terminal. You can change the IP address range.
[admin@MikroTik] > ip pool add name=L2TP ranges=10.1.101.50-10.1.101.100
I choose from our local IP address network.
Here is how it looks in MikroTik WebFig 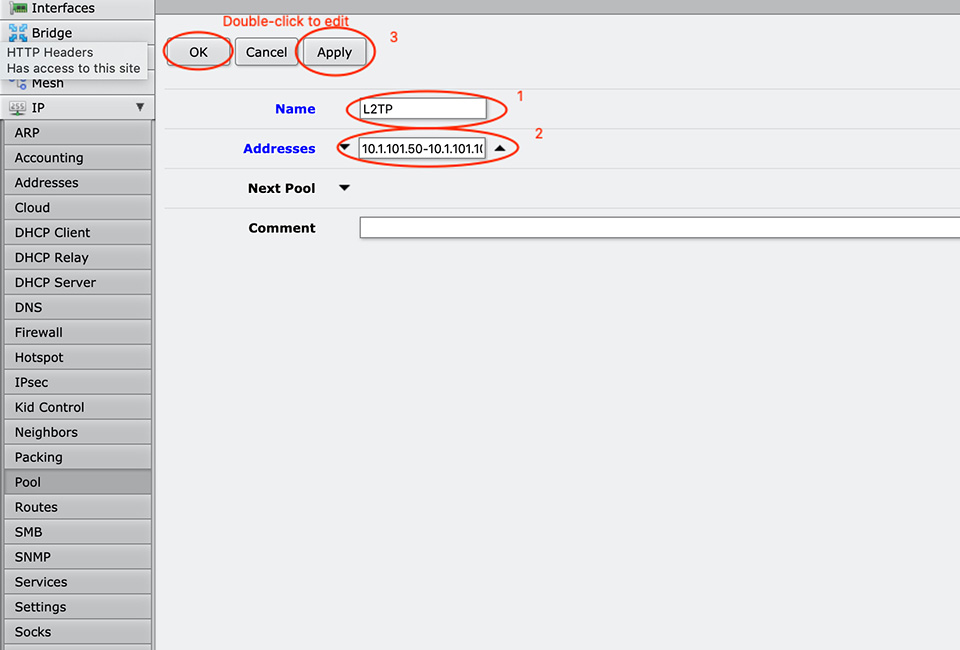
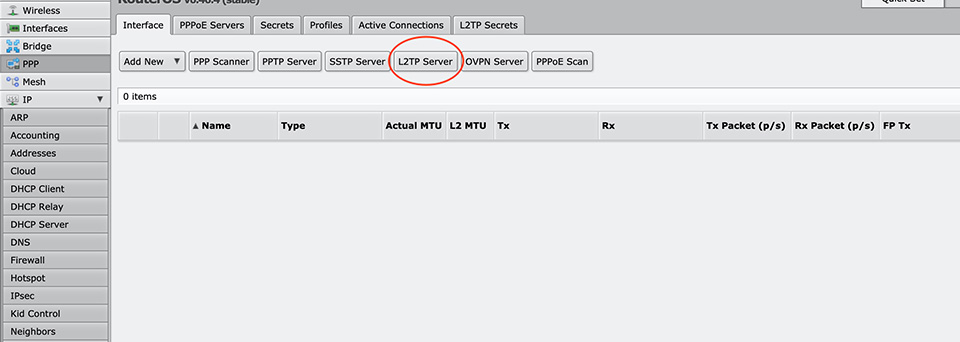
It is time to configure the L2TP server.
First of all, we have to еnable the L2TP server.
It is crucial to enable IPsec and set IPsec Secret!
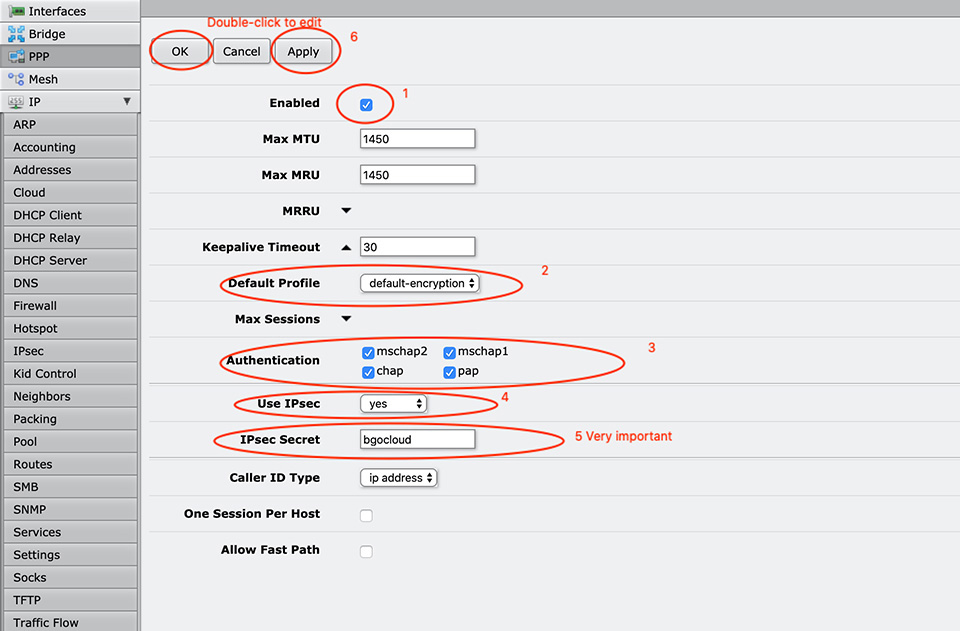
The command for this in MikroTik Router OS Terminal is:
[admin@MikroTik] > interface l2tp-server server set enabled=yes default-profile=default-encryption use-ipsec=yes ipsec-secret=bgocloud authentication=chap,mschap1,mschap2,pap
Let's take a look at Default Profile - Default-Encryption and make some changes there. 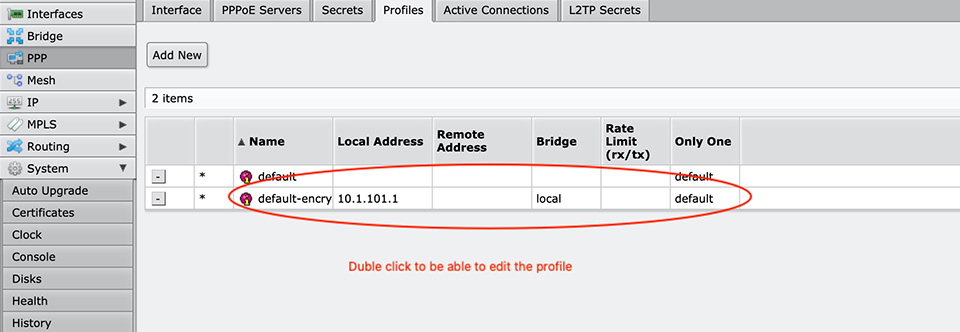
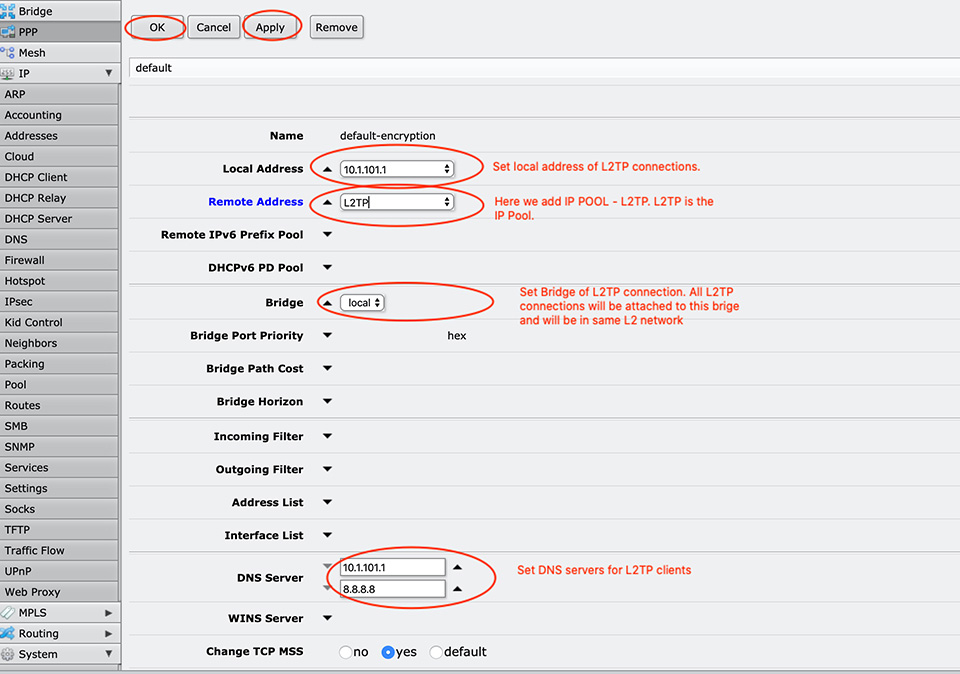
Comand for this in MikroTik Router OS terminal:
[admin@MikroTik] > ppp profile set default-encryption local-address=10.1.101.1 remote-address=L2TP dns-server=10.1.101.1,8.8.8.8 bridge=local
Maybe it is a good Idea here to enable DNS service on the router; otherwise, our L2TP client will not be able to access DNS server 10.1.101.1, and they can not open any website.
If you do not want to use your MikroTik as a DNS server, you can set DNS-servers of google 8.8.8.8 and 8.8.4.4.
But If you want to be able to make some static DNS records you have to enable DNS to your router, here is how this can be done:
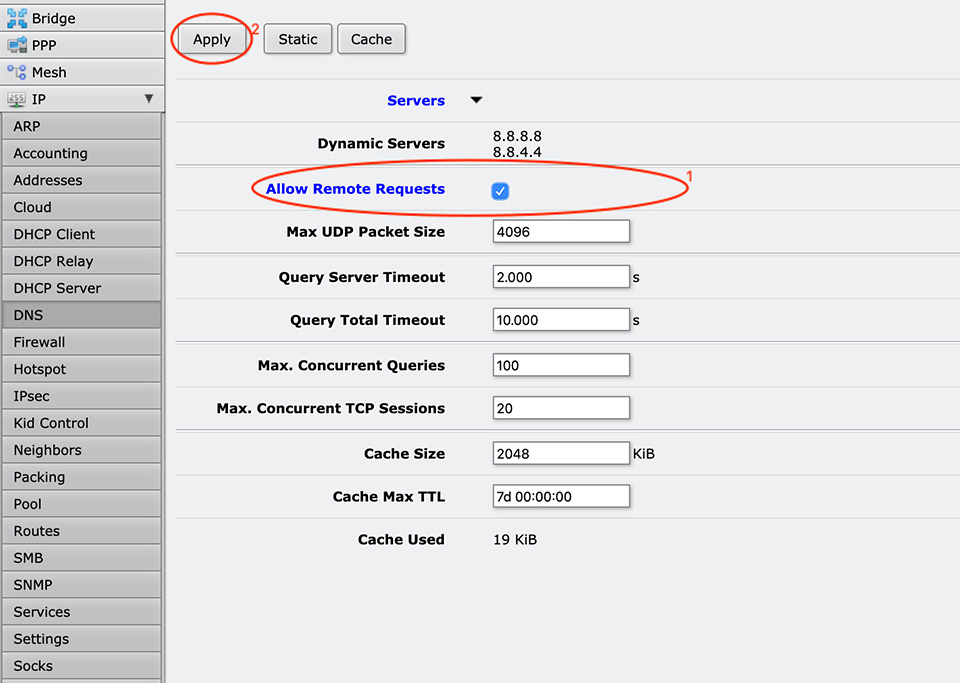
The Router OS command for terminal:
[admin@MikroTik] > ip dns set allow-remote-requests=yes
What we have?
We have a router with Public IP address 78.142.25.35 and Local IP address 10.1.101.1, enabled L2TP service, and enabled DNS service.
It is time to add our clients/users who will be able to connect to our router. 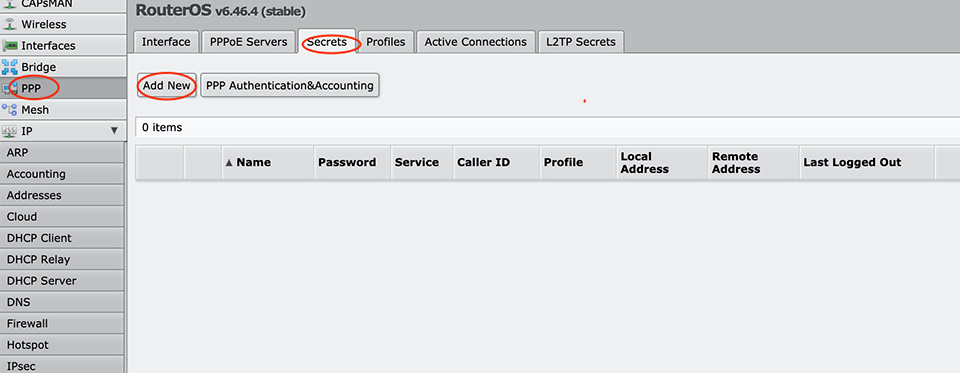
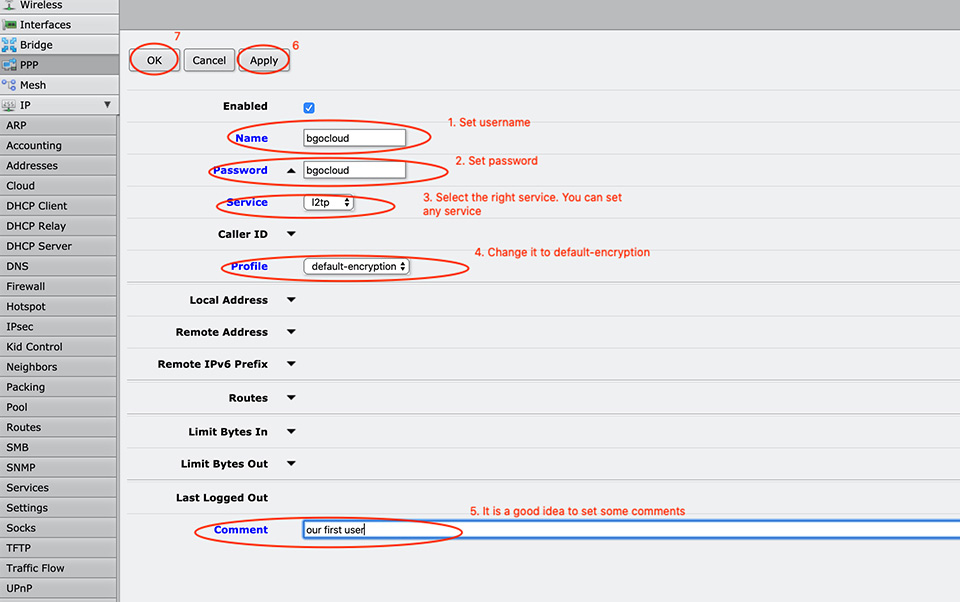
Here is the terminal command:
[admin@MikroTik] > ppp secret add name=bgocloud password=bgocloud profile=default-encryption service=l2tp comment="our first account"
Now we have a user with username bgocloud and password bgocloud.
Of course, you can change it with whatever you want! It is just an example! 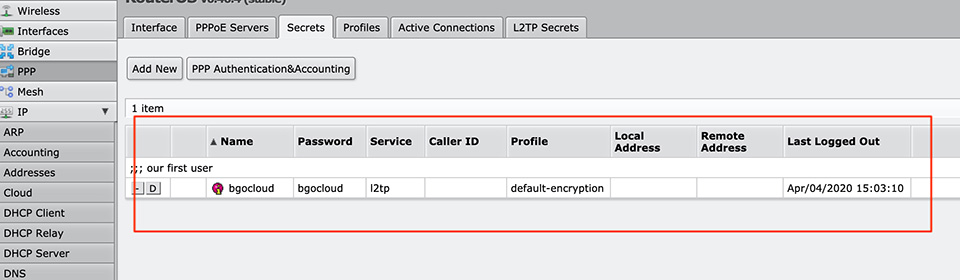
There is only one thing that we have to do, and it is very, very important!
We have to enable our NAT in Firewall!
Here is how it can be done: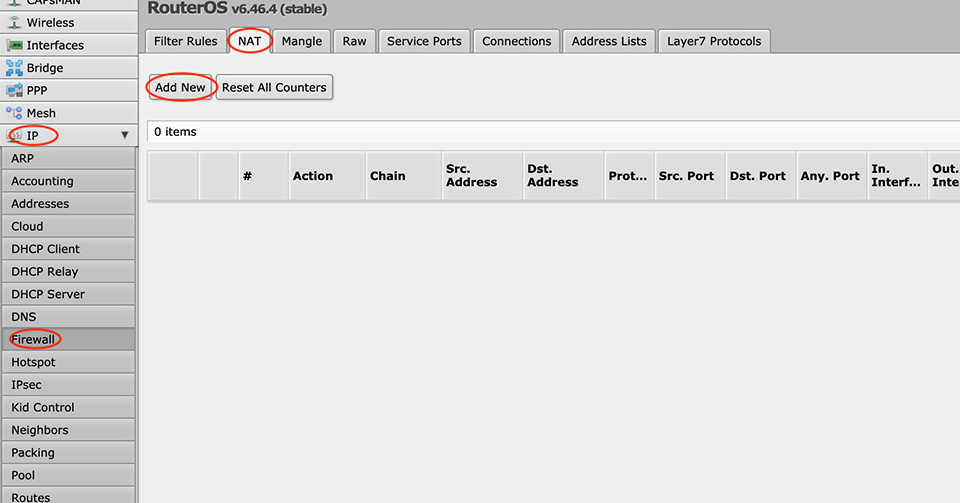
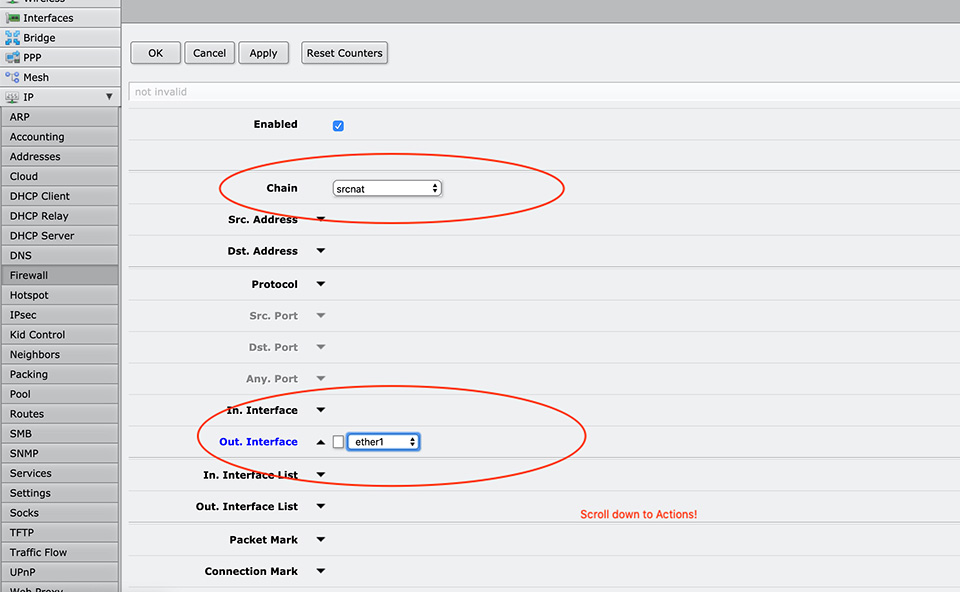
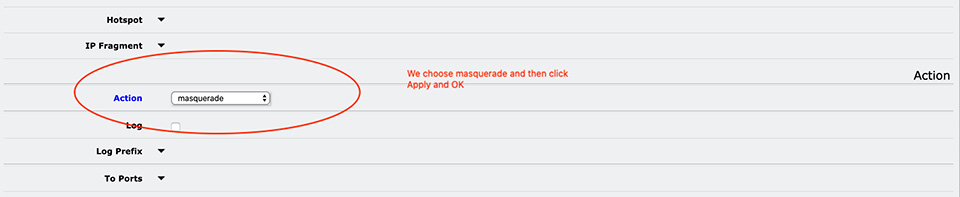
Here is the Router OS command for terminal:
[admin@MikroTik] > ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade
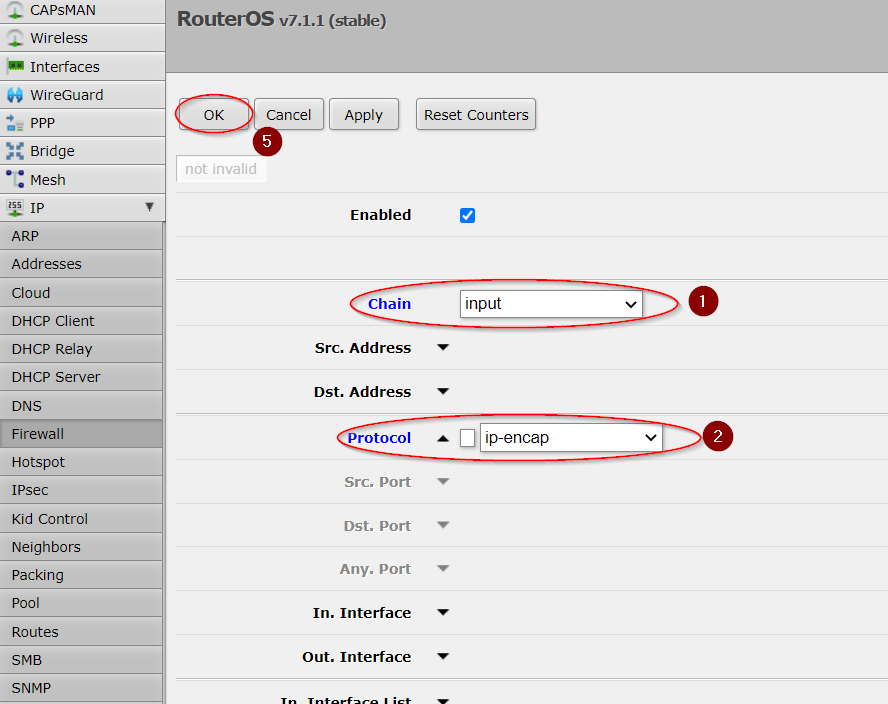
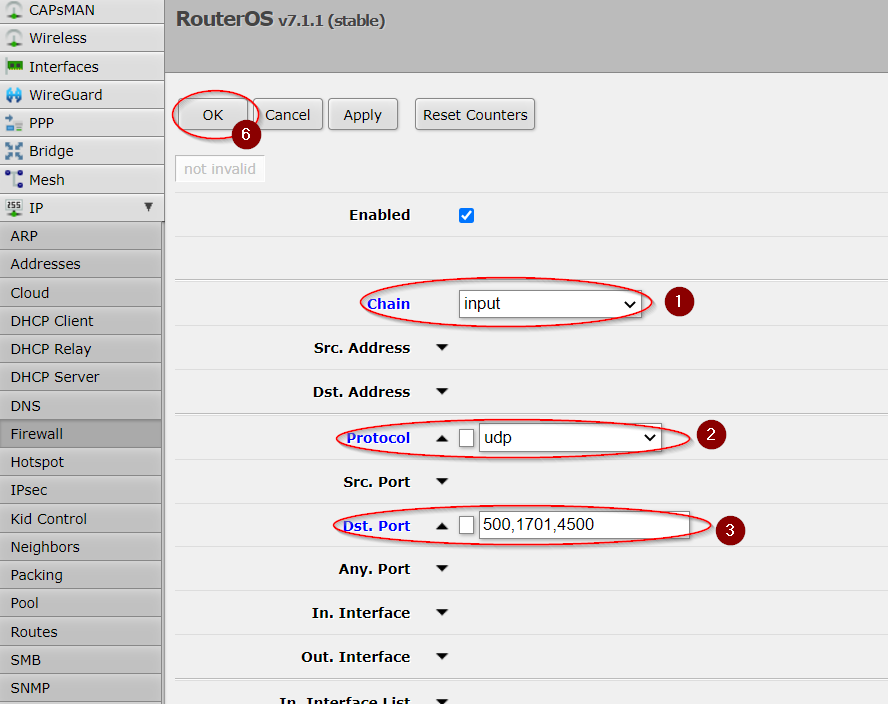
We also have to allow L2TP ports in our firewall!
Go to IP>Firewall Filter Rules and add these two rules:
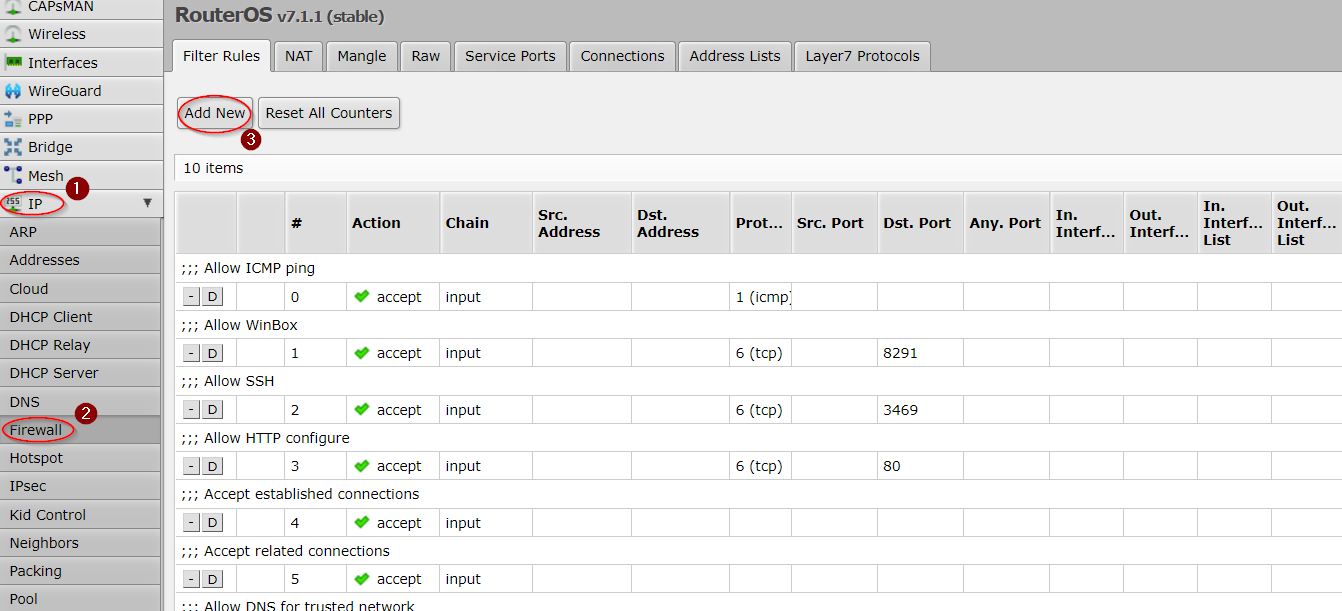
To change their priorities, you can simply drag them above the drop rules.
In RouterOS CLI you need to list all the rules, you can do that by using this command:
[admin@MikroTik] > ip firewall filter print all without-paging
It should output something like this:
Flags: X - disabled, I - invalid; D - dynamic
0 ;;; Allow ICMP ping
chain=input action=accept protocol=icmp
1 ;;; Allow WinBox
chain=input action=accept protocol=tcp dst-port=8291
2 ;;; Allow SSH
chain=input action=accept protocol=tcp dst-port=22 log=no log-prefix=""
3 ;;; Allow HTTP configure
chain=input action=accept protocol=tcp dst-port=80 log=no log-prefix=""
4 ;;; Accept established connections
chain=input action=accept connection-state=established
5 ;;; Accept related connections
chain=input action=accept connection-state=related
6 ;;; Allow DNS for trusted network
chain=input action=accept protocol=udp src-address=192.168.99.0/24
dst-port=53
7 ;;; PPTP VPN
chain=input action=accept protocol=tcp dst-port=1723 log=no log-prefix=""
8 ;;; Drop everything else
chain=input action=drop log=no log-prefix=""
9 ;;; Drop invalid connections
chain=forward action=drop connection-state=invalid
Enter these two commands, where X is the number of the first drop rule:
[admin@MikroTik] > ip firewall filter add chain=input action=accept comment="IPSec Pass" protocol=ipencap place-before=X
[admin@MikroTik] > ip firewall filter add chain=input action=accept comment="L2TP VPN" protocol=udp dst-port=500,1701,4500 place-before=X
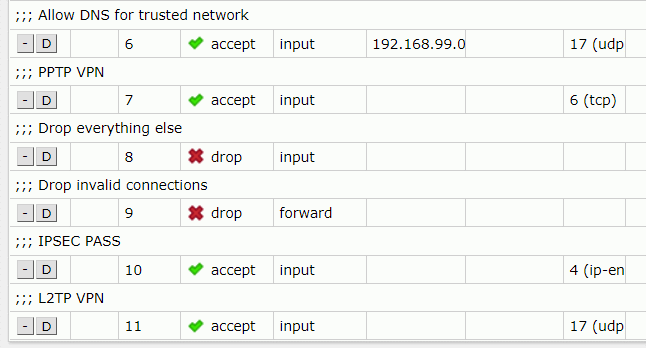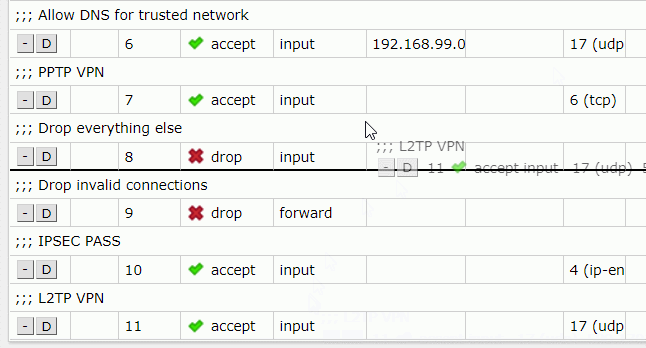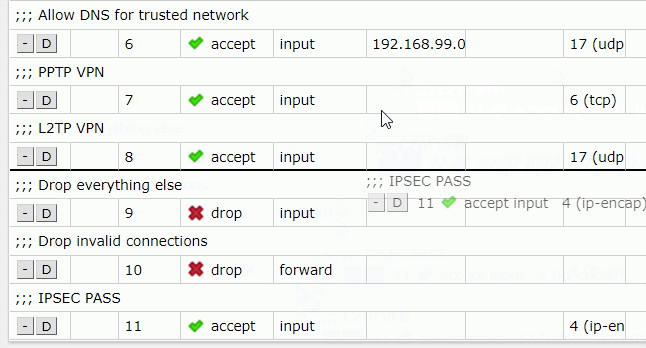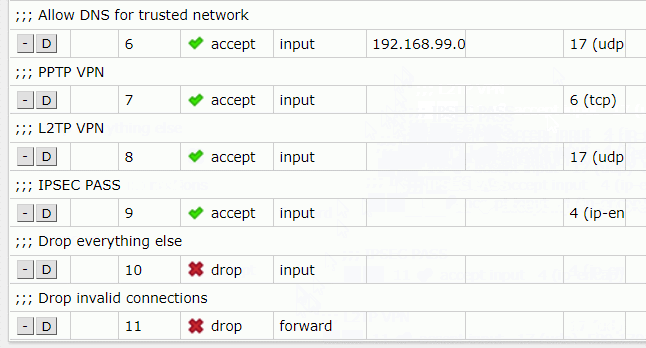
Then your Firewall filter rules should look like this
...
7 ;;; PPTP VPN
chain=input action=accept protocol=tcp dst-port=1723 log=no log-prefix=""
8 ;;; L2TP VPN
chain=input action=accept protocol=udp dst-port=500,1701,4500
9 ;;; IPSec Pass
chain=input action=accept protocol=ipencap
10 ;;; Drop everything else
chain=input action=drop log=no log-prefix=""
...
And that's it. We are ready to go!
Now it is time to set up our Apple devices L2TP clients how we can do this follow on this article: Set UP L2TP over IPSec VPN client on macOS
If setting up this server is hard for you, you can take a look at our fast and secure OpenVPN Hosting plans. Easier and quicker to set up, more secure and it's ready in 5 minutes.

